2020 Shaping Up to be a Record Year for Cyber-Criminals
by Olivia Infante, Associate Editor
In the past, cyber criminals had to be technical, creative, and savvy, not only to commit such crimes as holding data for randsom, but to evade the efforts of law enforcement. In 2020 there is a growing industry springing up in cyber-criminal enablement, where developers are creating entire platforms that can be used to target, penetrate, and encrypt unsuspecting company's data and most surprising of all, the software is free. All the developers ask in return for use of their software is a 20% cut of the user's profits.
If you thought the Coronavirus spread fast, imagine hundreds of thousands of enterprising individuals getting into the extorsion business without any startup costs, overhead, or technical training needed. According to security specialist James Ratcliff of Ratcliff IT, 2020 is going to be a "banner year" for cyber criminals", empowered and embolded by turn-key software available for download now., for free, on the dark web.
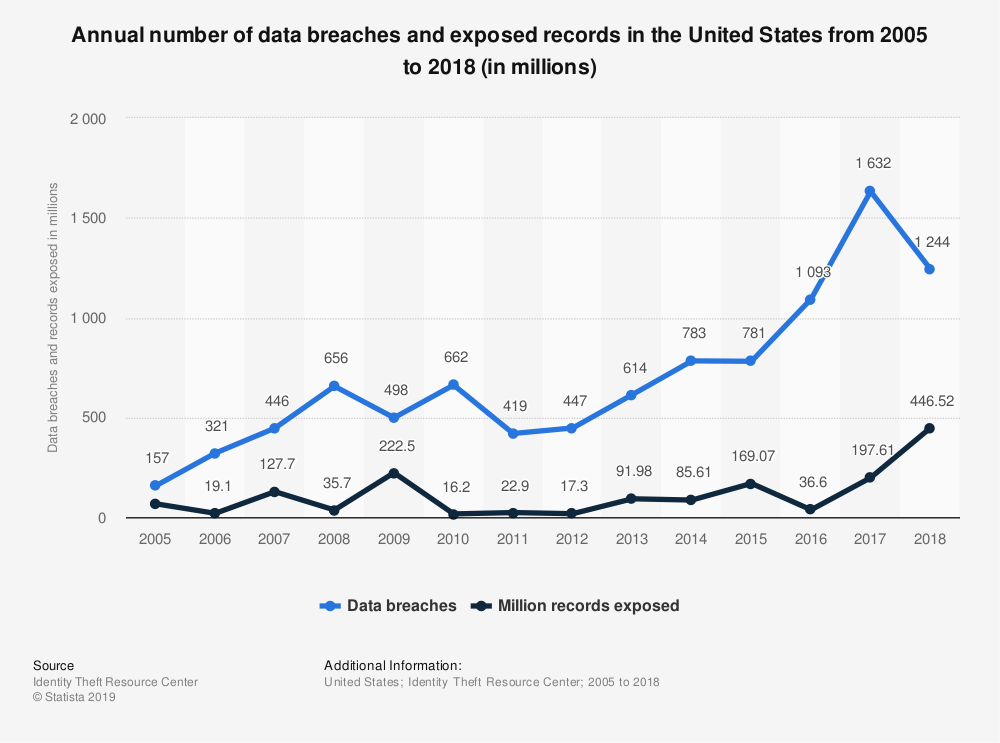
Just how bad did ransomware attacks get in 2019? The preliminary results are in!
Heimdal Ssecurity recently published some astounding statistics from ransomware attacks conducted in 2019:
- Two-thirds of ransomware attacks targeted state and local governments
- 55% of SMBs from the US paid hackers to recover their stolen data in ransomware attacks
- Over 500 US schools were affected by ransomware attacks in 2019
- Almost 70 US government organizations were infected with ransomware since January 2019
- A total of 140 US local governments, police stations, and hospitals have been infected with ransomware
- In the third quarter of 2019, the average ransomware payout increased to $41,000.
The most significant ransomware payouts of 2019
In the best-case scenario, victims of ransomware could simply wipe their systems and recover their data from offline backups. However, some organizations don’t keep any backups at all. Or worse, even if they do have copies of their data, sometimes they also end up being locked up by cybercriminals.
There are times when ransomware victims can decrypt their files with free ransomware decryption tools but sadly, there isn’t a decryptor available for all the ransomware strains out there. This sometimes leads to companies paying the ransom, being desperate to get their business back up and running.
A ounce of prevention is greater than a pound of cure
It's unrealistic to think that, as a member of the human race, you'll be able to pass through life without getting infected with some disease, virus, or bacteria during some point in your life. You do your best to exercise clean hygene, avoid obvious situations where infection can occur, but you know that you'll eventually get sick - it's life, afterall.
Business in 2020 need to have this same mentality. First, business need to avoid "getting sick" and take the necessary precautions to limit their exposure to viruses, phishes, and most of all, the deaded ransomware attacks. "Healthy habits" for company cybersecurity also need to incorporate the idea that, at some point, the company WILL get breached, and thus should have a rehersed, planned, and measure counter-response for the day in which that happens.
The National Institute of Standards in Technology, created by the U.S. Department of Commerce, is the gold standard when it comes to putting together a game plan for a solid defense while at the same time reducing the time it takes to detect and remediate a breach as it happens. (Most companies who get breached don't discover the intrusion for over 90 days!)
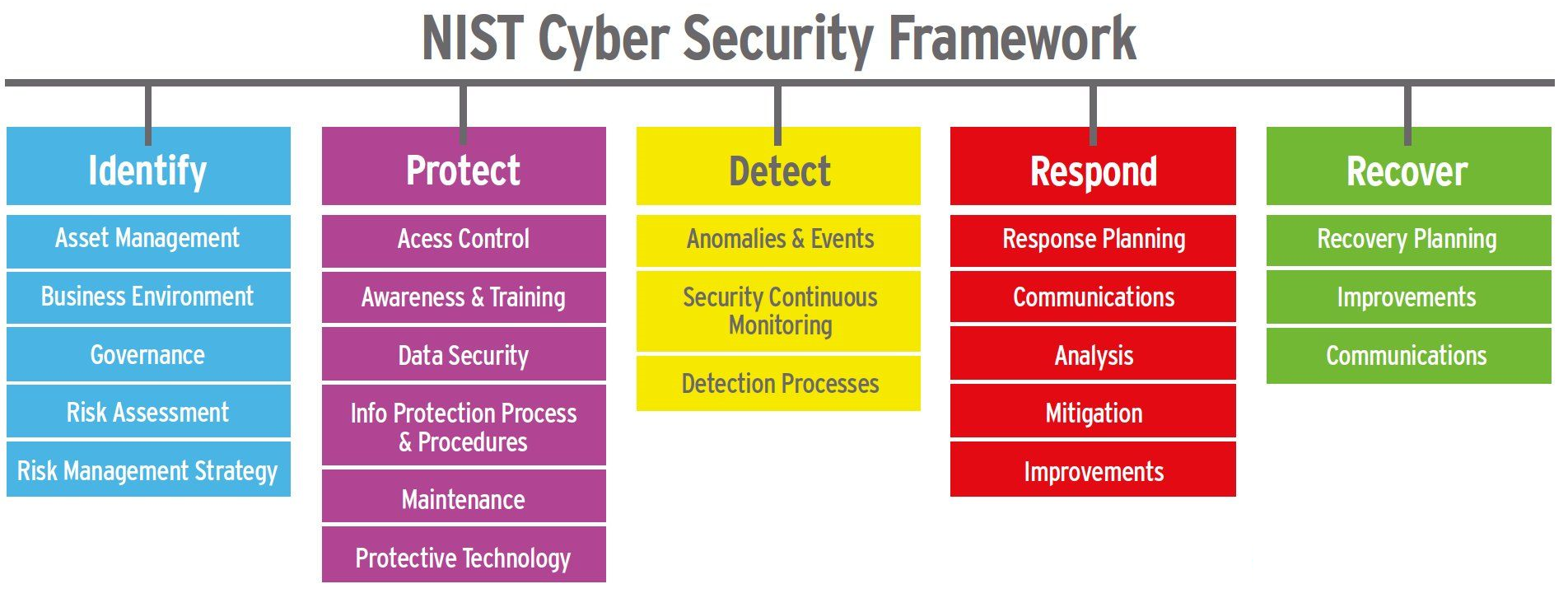
NIST - More than meets the eye
This plan seems simple enough, but the number of true NIST practitioners is woefully low. So low, in fact, that most major corporations are unbable to find qualified candiates to occupy the position of CSO (Cheif Security Officer). This difficiency in the workforce has forced businesses to either execute the duties of the CSO by "committee", or - more commonly - to oursource the function to thrid-party firms who offer "CSO as a Service".
The benefits of CSO as a Service
When planning to fight the battle of your life, you need someone on your side that can out-think, out-work, and out-perform your enemy. We've interviewed several companies that have chosen to go the vCSO route and have been very happy with the service they received. Some of their comments included (in summary):
- "We paid $5.000/mo for a very experienced vCSO who attened all of our security meetings, help us develop a detailed plan around employee training and education, negotiated with our other third-party security service providers, and helped us dramatically reduce our risk profile. Under his leadership we were able to qualify for cyber insurance and we passed the necessary compliance audits required of us from our upstream suppliers. The best part was, we didn't have to worry that he'd take a job somewhere else, especially since we were only paying his firm $5,000/mo!"
- When we interviewed another firm using vCSO, the company made the point that "if we hire our own CSO - assuming we couldl afford one - he'd be limited to his own knowledge and experience. Using a vCSO service, we got the benefit of an entire bench of talent, all of which brought a unique perspective to helping us deal with the ongoing and fluid demands of running our Security practice."
Want to Learn More?
If you would like to engage with a Trusted Advisor that can advise you on the best firms offering vCSO services to help you prevent, and ultimately respond to a breach, give our technical help desk a call at +1 (888) 711-3656 and we'll put you in contact with a trusted independent security specialist in your area.

About the Author: Olivia Infante is the Associate Editor of BizPhonics.com. She covers all of the recent developments in cybersecurity. She's been all over the globe, attending conferences, talking to analysts, and inteview cybersecurity experts to piece together a comprehensive view of which products and services work best accross a variety of attack surfaces.
